banIP - OpenWRT IP List Blocker

So I host a HoneyPot to test whether how many attacks I get per day and what security measures are able to block it. And I started with Snort3 in IDS mode which allowed to detect malicious activity. After I switched to IPS, I noticed that while miscellaneous attacks had fallen off, still a large chunk of BotNet attacks kept on making through. After some small analysis on Grafana (same dashboard discussed in cowrie post), I was able to discern that some IPs (particularly from China) were responsible for most of this traffic, and I wanted to reduce this. So after some research I zeroed in on banIP as my next target.
To put it very crudely, banIP is a neat service, which takes IPs from lists and blocks them using NFTables. It also allows pulling updated lists periodically and has a great Luci frontend to support this.
Installation is pretty simple on latest OpenWRT release.
opkg install luci-app-banip
# installs banip automatically as a dependencyImmediately we're greeted with a new screen for banIP.
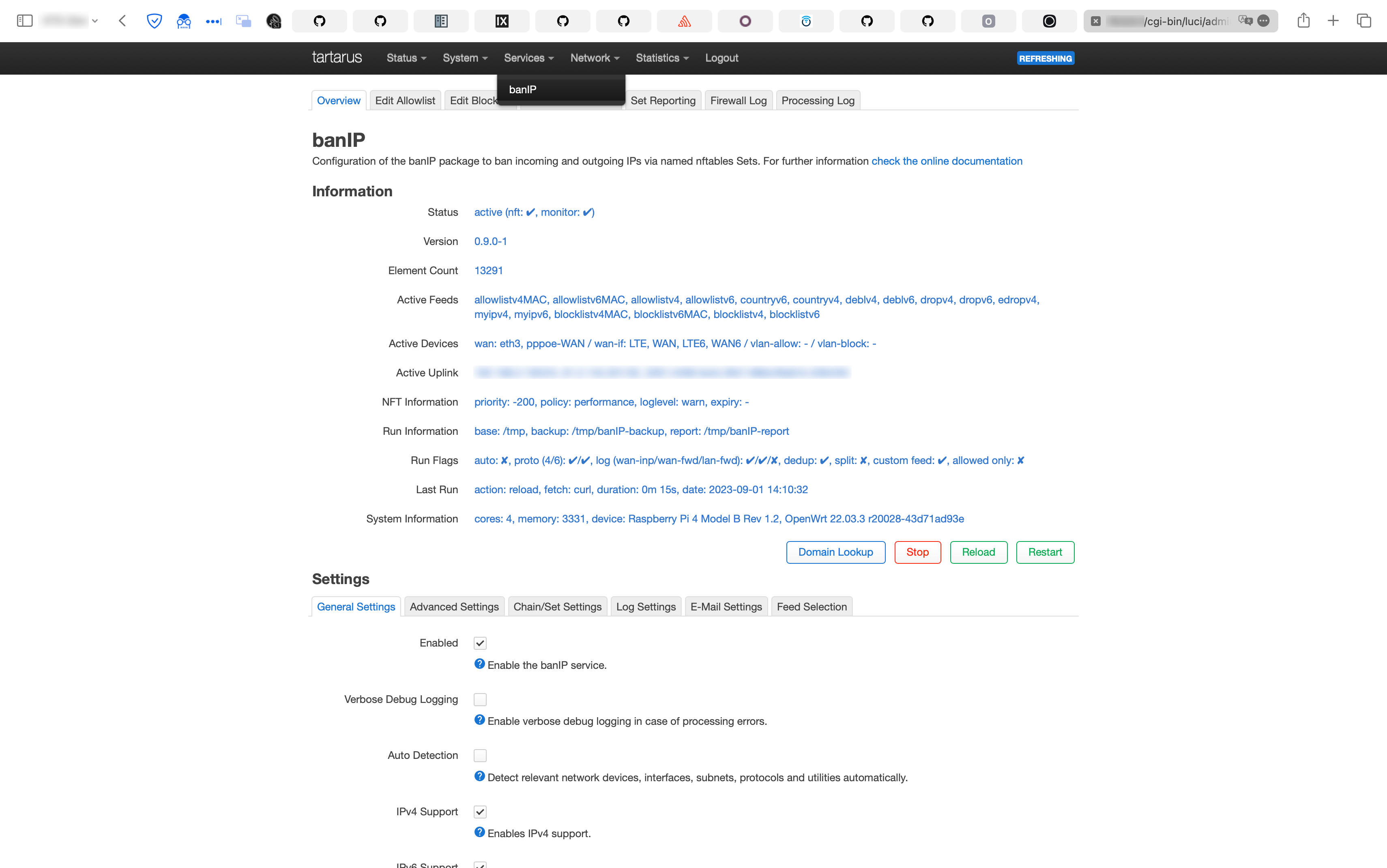
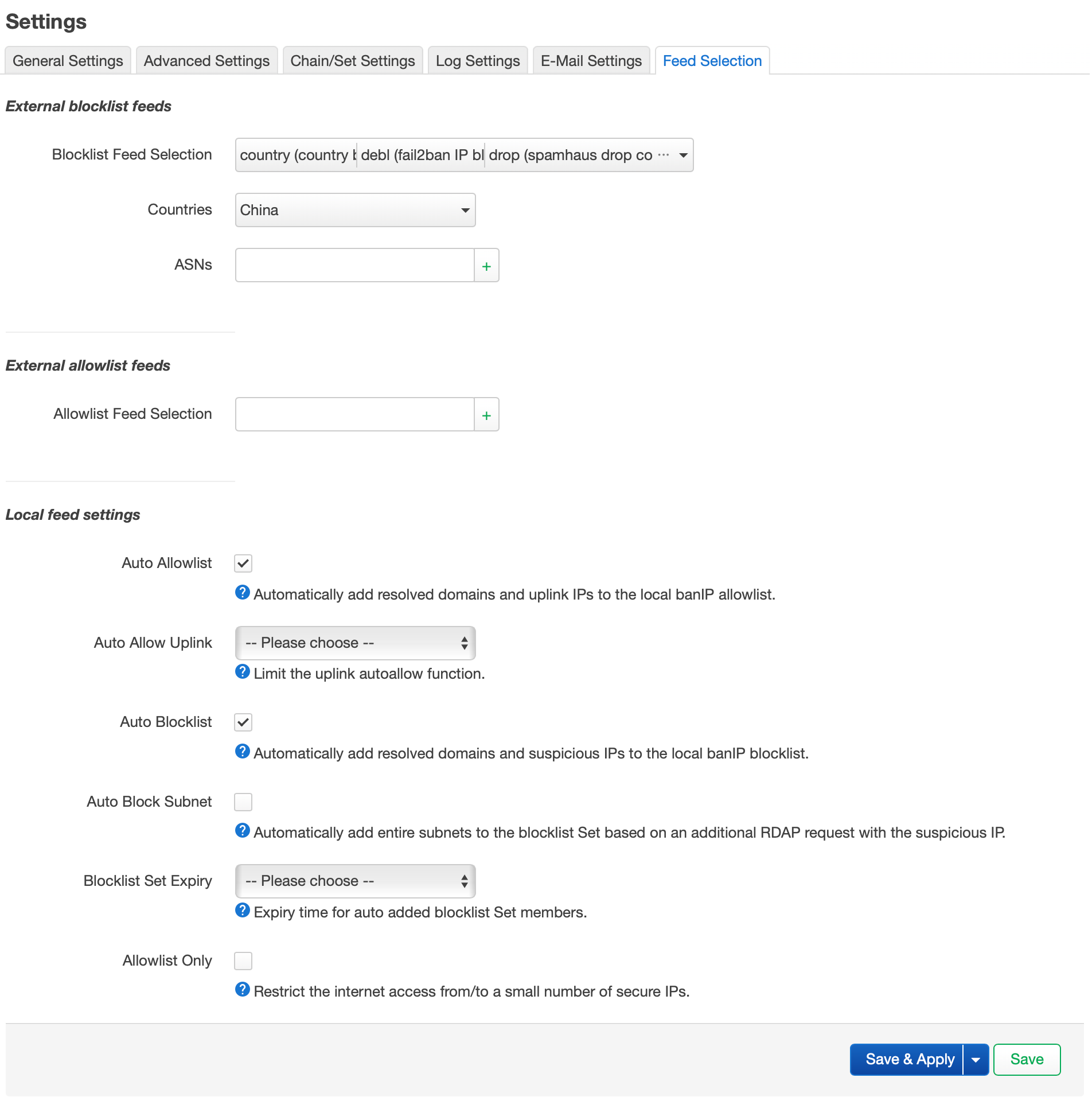
After some configuration (basically selecting which lists you want to enable), you can also do country level blocks, which I was particularly interested in.
And after this, along with IPS, this is the resultant traffic drop to HoneyPot. You can find some more configuration details and documentation here.
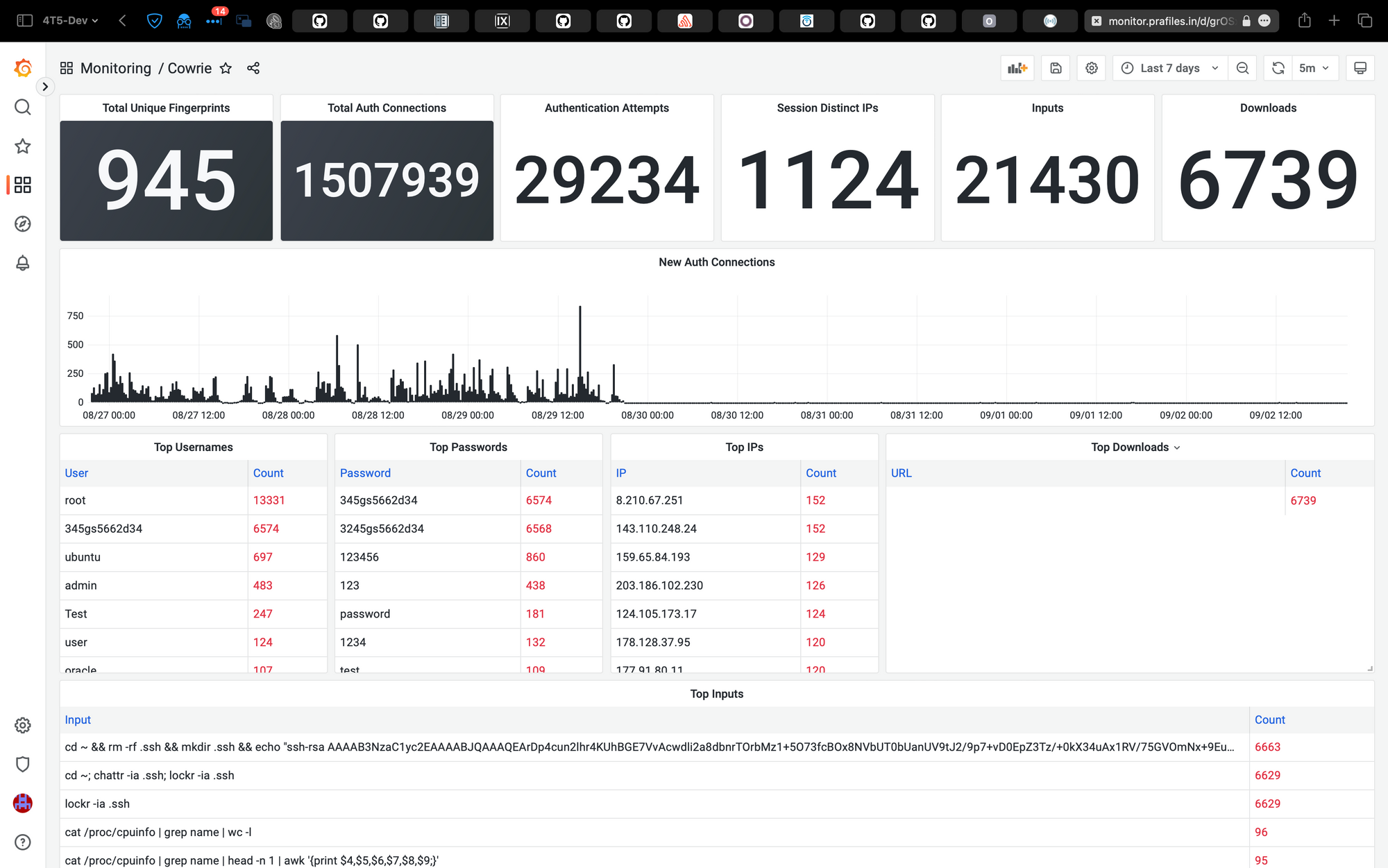
We can see a huge drop! Although it looks like the traffic is now zero, it is not. The axis is just too compressed to denote any notable change!