Mirai Botnet in 2021
Following my post about the HoneyPot, and this port is about one of those attacks. While Mirai is no more the hot news, the most number attacks, albeit I hope mostly useless, start from this simple bot. In fact, this is the list of unique malware download attempts on my honeypot.
Btw, if you’re curious, the original table looks like:
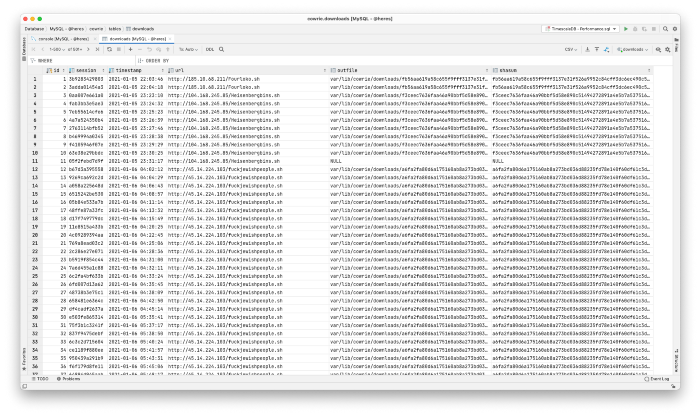
So going back to the original gist, most of them seem to be Mirai. How do we know this? Well if you curl the last link, you’ll get the signature Mirai script which essentially attempts to download any malware matching the device’s architecture. And in fact, same happens for most of them.
This looks super similar to this. There are some small modifications, but it’s a variant of the same.
You might wonder that what does Mirai do? Simply put, try basic password guesses on your “Smart Devices” and if they match, compromise them, and then use these new devices are stepping stone for more devices to attack. The big thing about Mirai is, that it’s entire source code was leaked publicly on Github which lead to lot of “versions” of this being in the wild. Though TBH, any basic security checkup will prevent this attack, as default password is a very basic attack vector that should be fixed right away.
Unfortunately, for this story, I’m going to use a Mirai Botnet that was taken down sometime ago, for which I did some malware analysis. I should state, this is a hobby of mine and there might be better articles and videos out there. However my aim is to document what I’ve learnt and what I want to share.
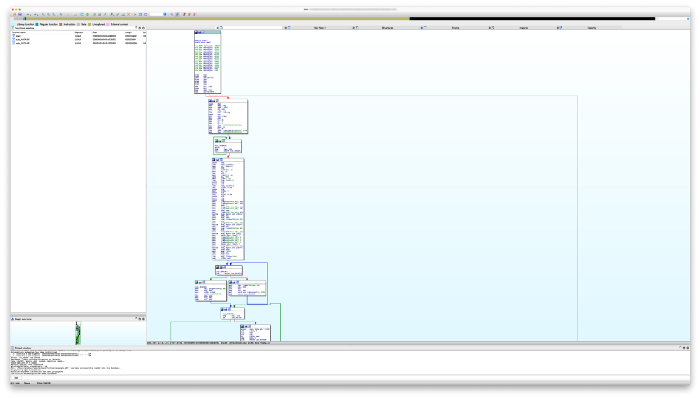
So I started by downloading the malware for x86 and loaded it into IDA. It gave me something, though not very useful. Using IDA Free is not very powerful anyway, and you can checkout videos like this for how that will make a difference. However, except for the payload, we do see the code structure very well, and it resembles that of Mirai significantly.
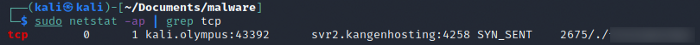
Since this wasn’t much helpful, and I wanted to get to the Command & Control Server, the clear option was to run this in an isolated VM with wireshark on. I use a Kali VM with no internet access initially and then a limited subnet. After starting the executable, a quick netstat reveals that there is only one connection.
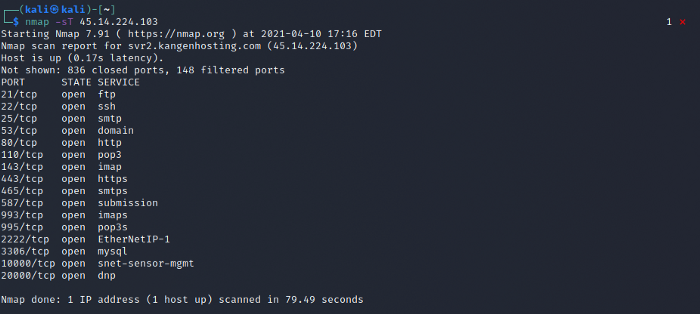
Running a port scan on the host revealed a lot of open ports. Bad security perhaps?
Filtering for the source and destination on Wireshark, I get that while the malware is actively trying to connect the port is being denied (the behavior when the port is not open). Perhaps someone has taken care of this C&C server already.
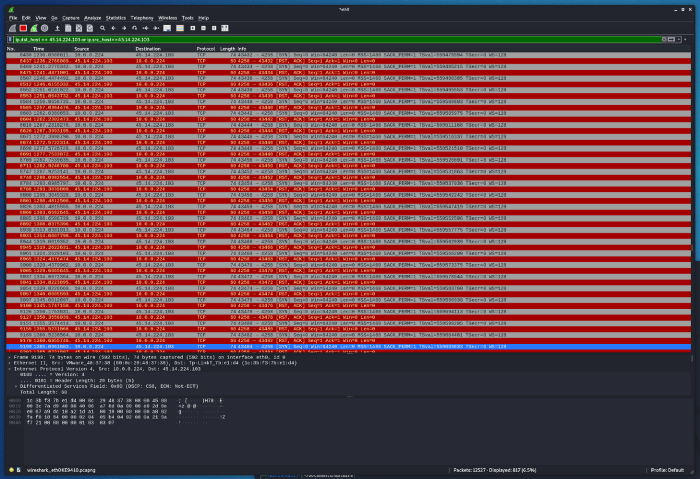
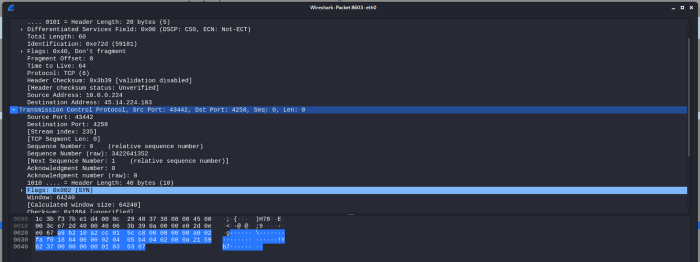
We can also see the destination for for the malware was port 4258, but it fails to connect, which we can verify from our port scan which we’d done above, as this port is not open.
In future, I’ll try to explore more malware binaries and Mirai’s source code as well.